Wednesday, October 24, 2007
Install GNU/Linux without any CD, floppy, USB-key, nor any other removable media
I have a server running CentOS 4 with internet on it. This server is without any CD Drive, floppy Drive, USB-key, nor any other removable media and its Remote server.
How do i install CentOS 5 on it? I have searched in various forums, posted in various forums.
After a long hour I have came to solution.
I am writting here what excataly I have done.
Since, I have net connection on current system,
1. I have downloaded ISO image of centos 5 (1 CD only)
2. mkdir /mnt/tmp
3. mount -o loop CentOS-5.0-x86_64-bin-1of7.iso /mnt/tmp
4. cp -a /mnt/tmp/isolinux/vmlinuz /boot/vmlinuzMy
5. cp -a /mnt/tmp/isolinux/initrd.img /boot/initrdMy.img
6. umount /mnt/tmp
7. Add entry to your /etc/grub.conf
title Fedora Core 2 Installation
root (hd0,0) kernel /boot/vmlinuzMy
initrd /boot/initrdMy.img
8. Reboot system
9. Now your is booted and ready for new installation.
10. Select installation method you want (FTP, HTTP or NFS probably). I have selected http
11. Give your Name server and ipdetails.
12. Give site & Dir (I have given)
mirror.stanford.edu
/yum/pub/centos/5/os/x86_64/
I think its ok to install now :)
Thursday, October 18, 2007
System Security Monitor root access
So, its good if you have system which automatically send a email notification via email whenever someone logs in as root on your system.
To configure the automatic email alert notification to a email address on each incident of root log on on the server, use the following guide.
Login to the server via SSH using as root ID.
- Ensure that you’re at home directory of root. The open up the .bash_profile for editing using pico or vi by typing one of the following commands at linux command shell:
pico .bash_profilevi .bash_profile - Scroll down to the end of the file and add the following line:
echo 'ALERT - Root Shell Access on:' `date` `who` mail -s "Alert: Root Access from `who cut -d"(" -f2 cut -d")" -f1`" user@example.com
Replace user@email.com with the actual email account address that you want to the root access alert notification been sent to. Note that you can change the text contains in the email alert too. The text starting with first ALERT is written as email body, and you can add in other info such as host name or change the wordings. The second Alert is the email title which you can change to your own too.
Note that you can change the text contains in the email alert too. The text starting with first ALERT is written as email body, and you can add in other info such as host name or change the wordings. The second Alert is the email title which you can change to your own too.
Now logout and login again as root, you should receive an email alert at your inbox. The security trick should works on most popular flavor of Linux such as RedHat, CentOS, Ubuntu, FreeBSD and etc.
Saturday, September 15, 2007
Trademark Problem
But you must be thinking in admin Linux blog I am talking about trademark what happen to this guy. Believe me I am not crazy.
One day I got this comment:
"
Dear Mr. Kumar,Your "Open Hearts" header presents a bit of a problem for us as we hold the international trademark for "Open hearts. Open minds. Open doors." We ask you, kindly, to please remove this statement from your blog. If you have any questions, please contact us at im@umcom.org. --The United Methodist Church.
"
"Open Hearts, Open Minds, Open Doors... Open Source" yes this Title Description is trademark to someone.
Now just I reshuffled this and made it to “Open Minds, Open Hearts, Open Doors... Open Source"
Hope this will not create any problem.
Thursday, September 13, 2007
Backup strategy
In computer world most important thing is DATA. No system can 100% secure or fault tolerance, so we always worry & care about data.
Various organization follows different back strategy. Like daily, weekly, monthly or yearly and at different levels.
Once my CEO asked me to design the backup system, and then I study various backup system, algorithms and architectures.
Then I come up with this backup architecture
Level 0 - Hard disk backup using RAID -1 mirroring, its purpose is to use in the case of hardware failure.
Level 1 – OS backup using rsnapshot. It is a file system backup utility based on rsyn, using rsnapshot; it is possible to take snapshots of your file systems at different points in time. Its purpose is to use in the case of OS failure.
Level 2 – Application data backup on same data center using Rsync. Its purpose is to use in the case of application failure.
Level 3 – Application data backup at remote location. Its purpose is to use in the case of data center failure.
As you move from level – 0 to level -3, you have to take more revisions like hours 1, day 1, week 1, and year.
I think this is quit good backup strategy.
Monday, June 25, 2007
Xen : virtualization software
Now I am writting about XEN , It is software that runs on a host operating system and allows one to run several guest operating systems on top of the host on the same computer hardware at the same time. Xen Software which enabling every server to support multiple virtual servers. It is the fastest and most secure virtualization software.
In Xen virtualization, a thin software layer known as the Xen hypervisor ( open source technology, developed collaboratively by the world’s best engineers at over 20 of the most innovative data center solution vendors, including Intel, AMD, Cisco, Dell, Egenera, HP, IBM, Mellanox, Network Appliance, Novell, Red Hat, SGI, Sun, Unisys, Veritas, Voltaire, and of course, XenSource ) is inserted between the server’s hardware and the operating system.
This provides an abstraction layer that allows each physical server to run one or more “virtual servers,” effectively decoupling the operating system and its applications from the underlying physical server.
In CentOS-5 Its In build
http://www.centos.org/
Some useful Link here
http://www.xensource.com/download/
http://www.xensource.com/media/xen/player.html
http://bits.xensource.com/Xen/docs/user.pdf
http://www.linuxjournal.com/article/8540
http://wiki.xensource.com/xenwiki/XenIntro
Friday, April 27, 2007
Virtualization : Basic Concepts
Similarly, Operating system virtualization is the use of software to allow a piece of hardware to run multiple operating system images at the same time.
a) Network virtualization
b) Storage virtualization
c) Server virtualization
Today, virtualization is in the forefront - helping businesses with scalability, security and management of their global IT infrastructure.
Virtualization can host multiple guest operating systems. Each guest operating system runs in its own domain, Virtualization schedules virtual CPUs within the virtual machines to make the best use of the available physical CPUs. Each guest operating systems handles its own applications. These guest operating systems schedule each application accordingly.
Full virtualization provides total abstraction of the underlying physical system and creates a new virtual system in which the guest operating systems can run. No modifications are needed in the guest OS or application (the guest OS or application is not aware of the virtualized environment and runs normally).
To know more on Virtualization:
Intro to Virtualization,
SearchServerVirtualization.com,
Red Hat Enterprise Linux Virtualization.
Monday, April 23, 2007
Change the default port for SSh user
eg. I want to run ssh service on port 99 instead of 22.
Make the following change.
open files
#emacs /etc/ssh/ssh_config
#emacs /etc/ssh/sshd_config
search for port ie is default port = 22
make port = 99
or
You can run on any port, But make sure other service not running on that port.
Thursday, April 19, 2007
web Based administration solution for Linux : webmin
how To Install Webmin:
# cd /usr/src
# wget http://prdownloads.sourceforge.net/webadmin/webmin-1.340-1.noarch.rpm
# rpm -ivh webmin-1.340-1.noarch.rpm
steps to install virtualmin & configure it:
login to webmin: ipaddress:100000
1) webmin -> webmin configuration -> webmin modulesInstall module -> from ftp or http url ->virtual min url is: http://download.webmin.com/download/virtualmin/virtual-server-3.201.gpl.wbm.gz
2) Enable https:yum install mod_sslin virtualmin config enable ssl for websites.
Configuring virtualmin:Enabled the subverion and mysql moduledisabled webalizerPostgreSQL setup and configuration enabled? yes.
3) If this server is going to use PGsqlPostfix configuration from webmin:servers->postfix->virtual domain->domain mapping lookup table: hash:/etc/postfix/virtual General options: Network interface for receiving mail: all [make sure that the hostname is something like sys.abc.comg is you are going to run the acb system here.]
4) dovecot configuration from webmin:webmin -> servers -> dovecot -> user login options -> Password authentication source -> unix shadow filestart at boot: yes
5) Webmin -> webmin configuration -> Ports and addressesaccess the webmin system: and then configure the port (eg 100000) for webmin listen and udp packets.
6) Webmin -> webmin configuration -> ssl encryptionAlso make webmin run on ssh.Enable SSL if available? yesRedirect non-SSL requests to SSL mode? yes
Monday, April 02, 2007
Check your memory !
These are few command which help u to debug your memory.
Simple stat.
#free
#du -h
#df -h
Some complex stat.
#cat /proc/meminfo
#dmesg | grep -n kernel
This command give you files have more than 100M usages.
#find / -size +100M -fprintf /root/big.txt '%-10s %p\n'
Tuesday, February 13, 2007
find out all failed login attempts via ssh/telnet
# grep "authentication failure" /var/log/messages|awk '{ print $13 }' | cut -b7- | sort | uniq -c
Thursday, February 08, 2007
find command with examples
find . -name "rc.conf" -print
This command will search in the current directory and all sub directories for a file named rc.conf.
find /usr/src -not \( -name "*,v" -o -name ".*,v" \) '{}' \; -print
This command will search in the /usr/src directory and all sub directories. All files that are of the form '*,v' and '.*,v' are excluded. Important arguments to note are:
* -not means the negation of the expression that follows
* \( means the start of a complex expression.
* \) means the end of a complex expression.
* -o means a logical or of a complex expression.
In this case the complex expression is all files like '*,v' or '.*,v'
The above example is shows how to select all file that are not part of the RCS system. This is important when you want go through a source tree and modify all the source files... but ... you don't want to affect the RCS version control files.
find . -exec grep "www.athabasca" '{}' \; -print
This command will search in the current directory and all sub directories.
find . -exec grep -q "www.athabasca" '{}' \; -print
This command is very important for process a series of files that contain a specific string. You can then process each file appropriately. An example is find all html files with the string "www.athabascau.ca". You can then process the files with a sed script to change those occurrances of "www.athabascau.ca" with "intra.athabascau.ca"
Tuesday, January 09, 2007
Recover Root Password of MYSQL
# /etc/init.d/mysql stop
Step # 2: Start to MySQL server w/o password:
# mysqld_safe --skip-grant-tables &
Step # 3: Connect to mysql server using mysql client:
# mysql -u root
Step # 4: Setup new MySQL root user password
mysql> use mysql;
mysql> update user set password=PASSWORD("NEW-ROOT-PASSWORD") where User='root';
mysql> flush privileges;
mysql> quit
Step # 5: Stop MySQL Server:
# /etc/init.d/mysql stop
Step # 6: Start MySQL server and test it
# /etc/init.d/mysql start
# mysql -u root -p
Enjoy ;-)
Monday, January 08, 2007
Recover Root Password In Liunx Machine
Probably the simplest way to solve a forgotten root password problem is to boot your system in the single-user mode.
If you are using LILO, at the LILO boot prompt (graphical LILO users can press Ctrl-x to exit the graphical screen and go to the boot: prompt), and then enter:
Code:
linux single
This will make you the "root" user without asking for a password. Once the system has booted, you can change the root password using the password command:
Code:
passwd
GRUB users will follow basically the same steps, except that the GRUB boot loader doesn't have a default boot prompt, but you can choose "e'' when the menu displays to edit the boot parameters. Just select the kernel line for the kernel you want to boot. Go to the end of that line and type "single" as a separate word, then press ENTER to exit the edit mode. Once back at the GRUB screen, press "b" to boot into single user mode.
Friday, January 05, 2007
Backup of DataBase from MYSQL
there is two method's i am using..
Method 1st :
mysqldump client is a backup program used to dump a database or a collection of databases for backup or transfer to another SQL server. The dump typically contains SQL statements to create the table, populate it, or both. However, mysqldump can also be used to generate files in CSV, other delimited text, or XML format.
The most common use of mysqldump is probably for making a backup of an entire database:
shell> mysqldump db_name > backup-file.sql
You can read the dump file back into the server like this:
shell> mysql db_name < backup-file.sql
Or like this:
shell> mysql -e "source /path-to-backup/backup-file.sql" db_name
mysqldump is also very useful for populating databases by copying data from one MySQL server to another:
shell> mysqldump --opt db_name | mysql --host=remote_host -C db_name
It is possible to dump several databases with one command:
shell> mysqldump --databases db_name1 [db_name2 ...] > my_databases.sql
To dump all databases, use the --all-databases option:
shell> mysqldump --all-databases > all_databases.sql
more u can read
Method 2nd:
find out where ur mysql sotre's the database generally default path will be:
:var/lib/mysql this is datadir=var/lib/mysql which is mention in mysql configuration file.
All the DB's u willfind on mysql dir, so u can copy the mysql dir.
this kind of backup used when u want to uninstall and then again install with different version.
simply move to other location mysql dir, and then copy that.
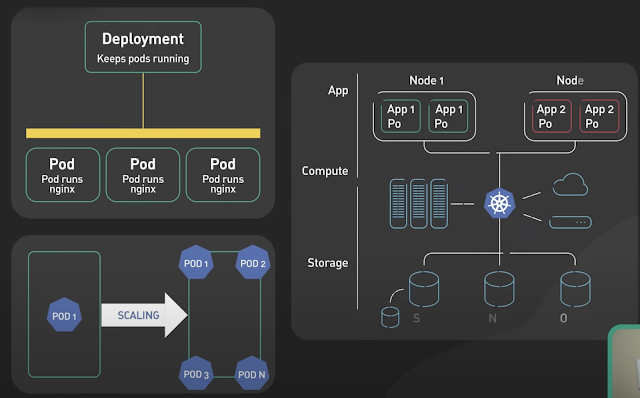
Basics of Kubernetes
Kubernetes, often abbreviated as K8s , is an open-source platform designed to automate the deployment, scaling, and management of container...
-
IOPS (input/output operations per second) is the standard unit of measurement for the maximum number of reads and writes to non-contiguous ...
-
MySQL's InnoDB storage engine data refresh every situation. This post from InnoDB down, look at the data from the memory to the InnoDB ...
-
The Unix top command is designed to help users determine which processes are running and which applications are using more memory or process...

